In a recent wave of cyber-attacks, the hacker group known as WhiteCobra has been identified as the culprit behind a series of malicious extensions targeting developers using popular code editors such as VSCode, Cursor, and Windsurf. These fraudulent programs are designed to steal access credentials and even cryptocurrency wallets, with the perpetrators going as far as to replace the extensions once they are detected and removed to continue their illicit activities.
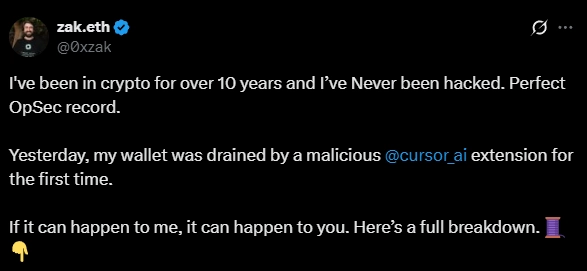
The discovery of this scheme was made by Zak Cole, an Ethereum developer, who reported that his cryptocurrency wallet was compromised after installing an extension that appeared legitimate. The extension boasted a professional icon, detailed description, and over 54,000 downloads, a figure that was artificially inflated by the scammers to lend credibility.
Fake Extensions and Necessary Precautions
Researchers at Koi Security have delved into the attack and traced it back to the WhiteCobra hackers. This group was responsible for stealing approximately $500,000 worth of cryptocurrencies in July alone, employing similar deceptive tactics. The current campaign involves at least 24 fake extensions available on the Visual Studio Marketplace and Open VSX, the official platform for Cursor.
The platforms’ compatibility with each other’s VSIX packages and their insufficient verification process for submitted extensions have created a fertile ground for these scams, according to Koi Security. Here is a list of the fake extensions identified:
VS Code Marketplace:
- awswhh by JuanFBlanco
- etherfoundrys by ETHFoundry
- givingblankies by EllisonBrett
- wgbk by MarcusLockwood
- blan-co by VitalikButerin-EthFoundation
- SnowShoNo by ShowSnowcrypto
- SnowShsoNo by Crypto-Extensions
- rojo-roblox-vscode by Rojo
Open-VSX (Cursor/Windsurf):
- ChainDevTools.solidity-pro
- kilo-code by kilocode-ai
- hardhat-solidity by nomic-fdn
- oxc by oxc-vscode
- solidity by juan-blanco
- solidity-ethereum-vsc by kineticsquid
- solidityethereum by ETHFoundry
- solidity-ai-ethereum by JuanFBlanco
- solidity-ethereum by Ethereum
- vscode-solidity by juan-blanco
- solidity-hardhat by nomic-fdn
- solidity by Crypto-Extension, among others.
Once the extension is downloaded, the main file (extension.js) seems innocuous, with code as harmless as any other extension. However, a subtle call redirects the execution to another script (prompt.js) which then downloads the malicious payload from Cloudflare Pages. The malware is tailored to the user’s operating system, with versions available for Windows, macOS ARM, and macOS Intel.
On Windows systems, the script is a PowerShell command that works alongside a Python script to download the LummaStealer malware. For macOS, the virus is a Mach-O binary from an as-yet unidentified family of malware. Koi Security has noted that WhiteCobra is a highly organized group capable of launching sophisticated campaigns and executing attacks within a remarkably short timeframe of less than three hours.
Advice for Developers
Given the nature of these attacks, it is crucial for developers to exercise caution when downloading extensions. Here are some steps to ensure safety:
- Verify the authenticity of the extension by checking the developer’s official channels.
- Be wary of names that closely mimic well-known extensions, as they are often used to deceive users.
- Exercise skepticism if a project is new but has rapidly accumulated a high number of downloads and positive reviews, as these could be artificially generated.
The WhiteCobra group’s actions serve as a stark reminder of the importance of vigilance in the digital space, particularly when it comes to tools that have access to sensitive information and systems. Developers are urged to remain vigilant and to take proactive measures to protect their work and assets from such cyber threats.
Source: Canal Tech
Like my content? Support me with a tip!