In a recent statement to BleepingComputer, Oracle has categorically denied any breach of its Oracle Cloud services. The denial follows claims made by a threat actor, identified as rose87168, who has been accused of attempting to sell what they allege are 6 million stolen data records from Oracle Cloud’s federated Single Sign-On (SSO) login servers.
“There has been no breach of Oracle Cloud. The published credentials are not for the Oracle Cloud. No Oracle Cloud customers experienced a breach or lost any data,”
– Oracle’s spokesperson
Threat Actor’s Allegations and Proof
Rose87168 released multiple text files purportedly containing a sample database, LDAP information, and a list of companies they claimed were affected by the breach. To back up their assertion of access to Oracle Cloud servers, the threat actor shared a URL showing a file upload to the login.us2.oraclecloud.com server containing their ProtonMail address.
BleepingComputer has questioned Oracle on how such an upload could occur without access, but Oracle has not provided further explanation, sticking to their denial.
Data Sale and Ransom Attempt
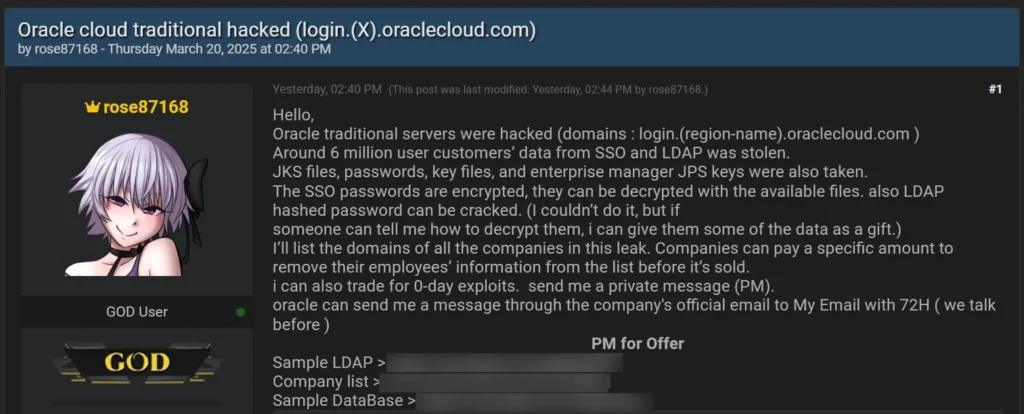
The threat actor is reportedly selling the data on BreachForums, demanding a high price or zero-day exploits in exchange for the stolen information. The data allegedly includes encrypted SSO passwords, Java Keystore (JKS) files, and other sensitive information from Oracle Cloud servers.
Rose87168 claims that the encryption on the SSO passwords can be bypassed with the files they possess, and LDAP hashed passwords are crackable. They have also offered to exclude specific companies’ data from the sale if they pay a certain amount.
Claims of Access and Vulnerability
The threat actor claims to have had access to Oracle Cloud servers for around 40 days and alleges they attempted to ransom the breach details to Oracle for 100,000 XMR after extracting data from the US2 and EM2 cloud regions. Oracle is said to have refused payment after requesting more information on the breach.
The breach is purportedly linked to a critical vulnerability, CVE-2021-35587, in Oracle Access Manager, part of Oracle Fusion Middleware, which could allow an unauthenticated attacker with network access via HTTP to compromise the system. However, BleepingComputer has not been able to verify the presence of this vulnerability in the software version used by Oracle Cloud.
Community Response and Analysis
Security researchers are divided on the issue. CloudSEK researchers have found evidence that may support the threat actor’s claims, suggesting a zero-day vulnerability or OAuth2 misconfiguration could be involved. They are analyzing a sample of the alleged stolen data, which includes potentially sensitive information.
Alon Gal, co-founder and CTO at Hudson Rock, posted on LinkedIn about the threat, noting Oracle’s resistance to the hacker’s demands. Trustwave SpiderLabs has also acknowledged the threat actor’s intentions to sell the data, indicating that the threat seems credible based on their analysis and the findings of other experts.
Ongoing Investigation
BleepingComputer has reached out to several companies whose data was allegedly compromised for confirmation. The article will be updated with any responses received.
As Oracle maintains its stance that no breach occurred, the cybersecurity community continues to investigate the claims. The truth behind the alleged breach remains elusive, with researchers and the threat actor presenting conflicting information. The community awaits further evidence to determine the actual status of Oracle Cloud’s security.
Source: BleepingComputer
Like my content? Support me with a tip!





